- Why is Compliance in the IT Industry So Important?
- Industry-wise List of IT Compliance Requirements
- Healthcare
- Education
- Fintech and Banking
- Manufacturing
- Additional Compliances Followed by All Industries
- How Regulatory Bodies are Approaching Technology Integrations
- How to Ensure Compliance-Readiness in Product Development?
- FAQs
Data security has been universally accepted as one of the foundational elements of business success. Influenced by digitalization and global connectivity reaching their zenith, it has become critical for companies to keep their and users’ data extremely secure. To ensure that businesses don’t fail in the process, several regulatory bodies have come to the forefront with their industry-wise compliances.
These compliances, once limited to data-heavy sectors like Fintech, Healthcare, eCommerce, etc., have slowly started making an appearance in technology adoption as well. In light of this, compliance readiness has become mandatory for any business operating with a focus on tech-powered digital offerings – a mandate that comes with its associated benefits and cost implications. For reference, the average compliance maintenance cost for organizations across all industries worldwide is $5.47 million, while non-compliance can cost them an average of $4,005,116 in revenue losses.
In this article, we are going to dive into the IT compliance regulations space by looking into the reasons why compliance is necessary, industry-wise regulatory compliances, and ultimately, the side effects of not meeting the compliance standards.
Why is Compliance in the IT Industry So Important?
IT compliance and security are necessary for the protection of clients, customers, employees, and companies’ privacy and for increasing the trust that the customers have in a business. When companies follow high privacy standards and digital security through compliance standards, their customers end up feeling secure when using their services.
Even if you leave customers out of the picture, the importance of IT compliance regulations in the US can still be seen as having a lasting impact on your business reputation and revenue. For example, the cost of non-compliance can add up to businesses losing $5,107,206 on average, heavy legal penalties, and lost business opportunities associated with the inability to partner with a company that operates in a compliance-heavy geographical area.
With industry compliance and regulations becoming so prevalent in the digital space, why are businesses still struggling with their adherence? Here are some reasons that we have identified after being a part of over 300 businesses’ digital journey.
- BYOD: Allowing employees to use their devices for work saves a huge amount of money. But in the absence of a proper BYOD policy, companies also lose the necessary focus to remain compliant.
- Third-Party Vendor Management: Vendors are extremely important when it comes to helping businesses operate. However, by transferring data to a third-party vendor you open yourself to vulnerabilities and data breaches.
- Software Updates: The modern-day technology space is constantly upgrading. To keep up with it, software companies are releasing new updates frequently. However, time constraints are keeping businesses from updating their software in real time, leading to the inability to remain safe and up-to-date with compliance.
- IoT: The Internet of Things connects smart devices. But security in IoT networks is still subpar, so you need to ensure that the devices are frequently tested for breaches or that the devices are connected to a network that cannot access sensitive data.
Now that we have looked into the reasons why the industry compliance standards are critical to adhere to, let us get down to industry-wise regulations and the ways you can ensure that your product/businesses are aligned with them.
Industry-wise List of IT Compliance Requirements
While every industry is different, the crux of IT regulatory compliance across all the different sectors is more or less the same – the protection of users’ data and business information from malicious parties.
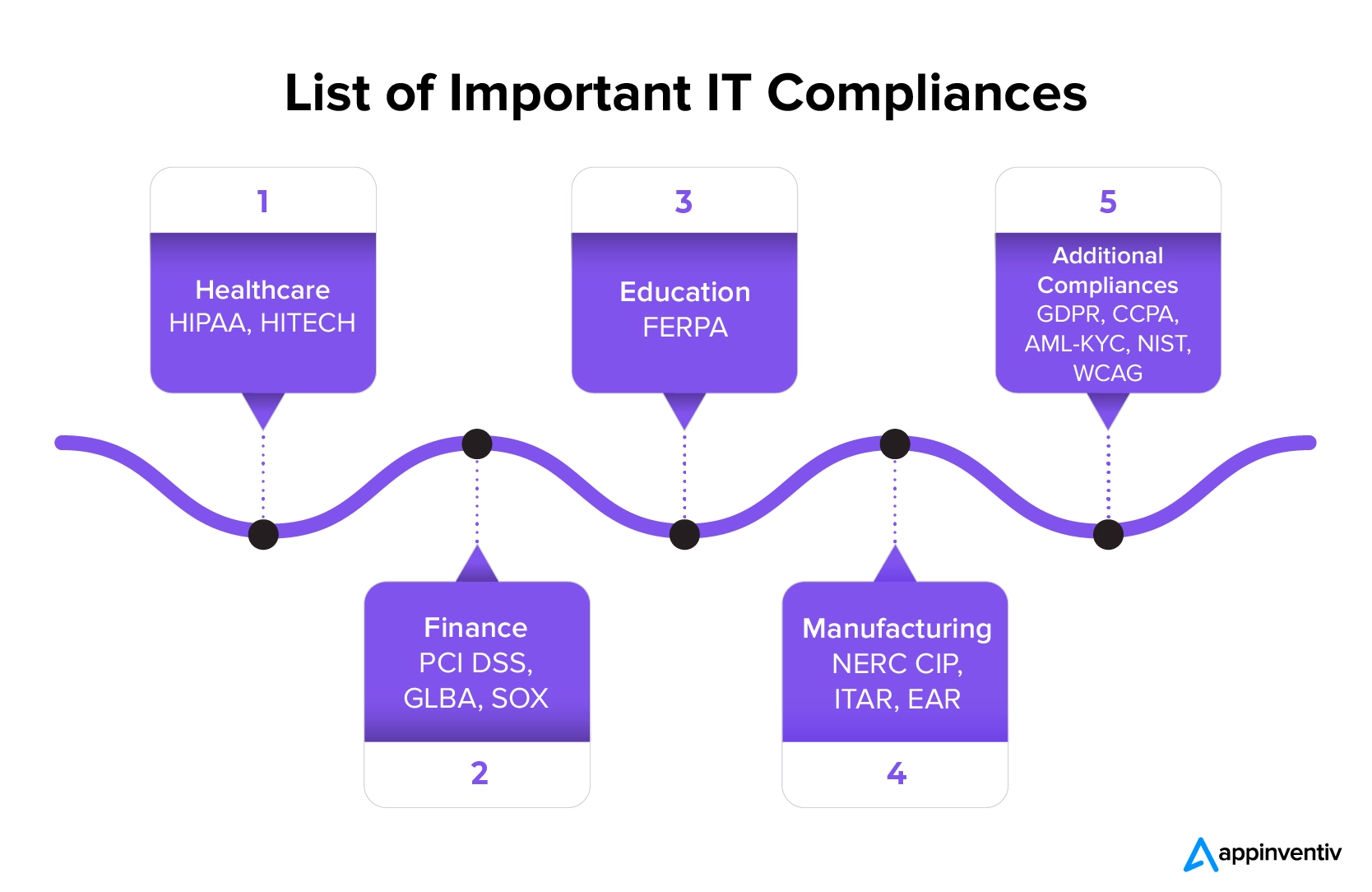
Healthcare
While there are a multitude of healthcare IT compliances on a global scale, HIPAA and HITECH are two of the most important compliances generally followed by businesses in this space. At Appinventiv, we follow both these compliances along with other ones in our software product development efforts. Outcome? Our clients – LIVIA, Diabetic U, and Shoona were compliance-ready the day they left our factory.
HIPAA
The Healthcare Insurance Portability and Accountability Act (HIPAA) highlights the usage and disclosure of health information to uphold patients’ privacy. The healthcare IT security compliance rule is built to guarantee that individuals’ health information is safeguarded while enabling the information flow needed for the promotion of high-quality healthcare.
To align with HIPAA compliance in the healthcare industry, all entities must:
- Make sure that the integrity, confidentiality, and availability of electronic protected health information (e-PHI) is HIPAA compliant.
- Identify and protect against expected threats to information security
- Protect against impermissible use or disclosure of data that are not allowed by the compliance
HITECH
The next healthcare IT compliance is the Health Information Technology for Economic and Clinical Health (HITECH) Act. It was brought into existence to promote the meaningful use and adoption of health information and technology. It looks into the security and privacy concerns linked with the electronic transfer of health information.
To comply with HITECH compliance in healthcare industry, organizations should:
- Protect patients’ e-PHI
- Generate all the prescriptions electronically
- Implement a clinical decision support system
- Use computerized provider order entry (CPOE) for laboratory, medication, and diagnostic imaging orders
- Offer timely patient access to the electronic files
- Participate in health information exchange
- Be a part of public health reporting
- Notify all the affected individuals within 60 days of the discovery of a breach of unsecured protected health information
Education
Educational institutions work with sensitive employee and student information, research data, and information from government bodies. To safeguard this dataset, organizations need to maintain adherence to FERPA compliance.
The Family Educational Rights and Privacy Act (FERPA) is a federal law of IT governance in the United States that safeguards the data and privacy of students’ education records. It gives them and parents control over the education records and restricts educational institutes from revealing personally identifiable information in the education records.
Here are the top FERPA IT compliance regulation requirements:
- Perform mandatory FERPA training for administrators, teachers, or other school officials
- Remind students of their rights annually
- Give consent that allows parents or eligible students to view records at any time
- Protect students’ personally identifiable data
Fintech and Banking
Being one of the most targeted industries among hackers, the finance software domain invites stricter restrictions from regulatory compliance compared to what is imposed on other industries. Here is the list of compliance in the finance industry that should be followed by businesses in this sector.
PCI DSS
The Payment Card Industry Data Security Standard (PCI DSS) is a combination of security standards built to guarantee that every company that accepts, processes, stores, and transmits users’ card information should maintain a safe environment. Our fintech developers are well versed in the nitty-gritty of compliance – an expertise reflected in the USA MedPremium project which achieved PCI DSS compliance the day it was deployed.
Here’s what the IT compliance for financial institutions entails:
- The PCI compliance calls for the installation and maintenance of a firewall configuration that would safeguard cardholders’ information
- Do not utilize vendor-provided defaults for system passwords
- Protect the data stored locally
- Encrypt the transmission of cardholder data across all the open public networks
- Utilize and routinely upgrade anti-virus software
- Build and maintain secure applications and systems
- Restrict the access to cardholder data by what businesses strictly need to know
- Track and scan every access to the cardholder data and network resources
- Regularly test processes and security systems
- Maintain a policy that focuses on information security
GLBA
The Gramm-Leach-Bliley Act (GLBA) applies to every financial institution that offers financial or investment advice, insurance, or loans to their clients. This compliance in the insurance industry mandates institutions to reveal how they protect customers’ information and what information-sharing policies have they put in place.
Here are the rules to be followed by GLBA IT compliance for financial institutions:
- Financial privacy: The financial privacy rule highlights how financial institutions gather and distribute private finance information. They should offer the clients an option to opt out of the information-sharing policy annually.
- Safeguard: Safeguard-based rules determine how institutions should use security measures to protect their customers’ data from cyber threats. These measures consist of using proper software, employee training, and testing software for vulnerabilities.
- Pretexting: The pretext part of the compliance in finance industry limits businesses from collecting information under pretenses.
Sarbanes-Oxley Act
The Sarbanes-Oxley Act (SOX) is another mandatory compliance in banking industry financial space. It calls for a transparent and complete disclosure of the company’s financial data. Every publicly traded company, a company launching its IPO must meet this standard. The standard makes it mandatory for companies to reveal accurate and full financial information so that the stakeholders can make informed investment decisions.
Here are the requirements of the popular fintech industry compliance and regulations in US
- Provide financial statements which have been audited by a third party to the SEC
- Report material changes to the public
- Design, implement, and test internal controls
- Compose an annual statement on the internal controls and their range, signed by the management and audited by a third-party auditor
While PCI DSS, GLBA, and SOX form three of the most important fintech compliances in the US, some other regulations that businesses must be wary of include Dodd-Frank, EFTA and Regulation E, CFPB, SOC 2, and ECOA.
Manufacturing
Like other industries, manufacturing businesses are also responsible for protecting employees, clients, organizational, and government data. Here are the different compliances they should adhere to.
NERC CIP
The North American Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP) compliance in the manufacturing industry is built to protect the integrity of all the utility infrastructure across North America. Every bulk power system owner, operator, and user should adhere to the NERC-approved Reliability Standards.
The prerequisites for meeting NERC CIP compliance in manufacturing industry include:
- Identify and classify all the assets
- Allocate an official to security-related matters
- Build and manage asset protection policies
- Offer security awareness training to employees
- Conduct thorough employee background checks
- Build access management controls on an as-need basis
- Develop electronic security perimeters – physical or virtual
- Manage all the secure remote access points
- Create and follow physical security plans and perimeters
- Maintain the system security controls with management of ports and services, patch management, security event logging, malware prevention, management of shared accounts, and credential management
- Create a cyber security incident response strategy that would also include continuity of operations, recovery plans, backup, and restoration
- Maintain vulnerability management and change comprising of management of transient cyber assets
- Protect BES cyber system information via categorization and protection of information and media disposal
- Build safe control center communications
- Bring supply chain security policies in place
ITAR
The International Traffic in Arms Regulations (ITAR) looks into the development, export, and import of all defense articles, the furnishing of all the defense services, and the brokering of defense articles. Its primary goal is to prevent defense-related items and data from getting into the wrong hands.
The requirements for ITAR compliance in the industry are as follows:
- Register with the State Department
- Incorporate a documented ITAR compliance program which would comprise tracking and auditing of all the technical data
- Take steps to safeguard data specific to items on the U.S. Munitions List
EAR
Export Administration Regulations (EAR) regulate the export, reexport, and transfer of less sensitive military items, commercial items having military applications, and purely commercial items without obvious military usage.
Here’s what the EAR compliance information security comprises:
- Classify your item using the Commerce Control List
- Establish written export compliance standards
- Develop a continuous risk assessment of the export program
- Create a manual of policies and procedures
- Provide ongoing compliance training and awareness
- Conduct continuous screening of contractors, customers, products, and transactions
- Adhere to recordkeeping regulatory requirements
- Compliance monitoring and audits
- Create an internal program for handling compliance issues
- Complete appropriate corrective actions in response to export violations
Additional Compliances Followed by All Industries
While those listed above were industry-wise lists of IT compliance standards, there are some complementary regulations as well which are followed by businesses in addition to these. Let us look at them as well.
GDPR
The General Data Protection Regulation (GDPR) is the toughest privacy and security law in the world. The regulation was put into effect in 2018 to protect the privacy and security of citizens in the EU. GDPR applies to any organization that processes the personal data of or supplies goods and services to EU citizens or residents.
When we were working on Slice, the moment we heard the idea we knew that we would have to prepare it for GDPR – something that we achieved by following the requirements to the t.
Here’s what GDPR IT regulatory compliance comprises:
- Conduct information audit around EU personal data
- Inform customers why you’re using and processing their data
- Assess the data processing activities and better data protection with strategies like organizational safeguards and end-to-end encryption
- Build data processing agreements with the vendors
- Appoint a data protection officer (if required)
- Allocate a representative in the EU region
- Know what to do in case of data breach
- Comply with all the necessary cross-border transfer laws
CCPA
The California Consumer Privacy Act (CCPA) gives California patrons control over the information that businesses generate from them. The CCPA rules apply to every for-profit business that operates in California and does the following:
- Have a gross annual revenue of more than $25 million
- Purchase, sell, or distribute personal information of 100,000 or more California consumers, devices, or households
- Generate 50% or more of their yearly revenue from the sale of California residents’ information
The requirements for meeting CCPA compliance in the industry include:
- Inform consumers of the intention to collect their data
- Provide users with direct and easy access to the privacy policy
- Give consumers their information within 45 days of the request
- Delete the personal data of consumers based on their request
- Allow the consumers to cancel sales and marketing campaigns that gather their personal information
- Update the privacy policy every year
NIST
The voluntary framework, National Institute of Standards and Technology (NIST) cybersecurity framework empowers businesses across all sizes to understand, handle, and lower their cybersecurity risks.
Here are the requisites for the NIST IT security compliance:
- Identify and categorize all the data that have to be safeguarded
- Perform timely risk assessments for establishing baseline controls
- Set up the baseline for minimal controls to protect information
- Record the baseline controls in a written manner
- Build security controls around all the online and IT systems
- Continuously track performance to gauge effectiveness
- Continuously monitor all your security controls
AML-KYC
A subset of AML, the Know Your Customer (KYC) process is conducted to check and verify the identity of every customer and prevent illegal activities from happening in the software, such as money laundering or fraud. We have helped a number of our clients including Slice, Exchange, Asian Bank, etc. adhere to KYC-AML compliance in the IT industry. How? By following the basics of compliance in its entirety.
- Perform Customer Identification Program – Gather data around Name, Address, Contact number, Nationality, Date of birth, Place of birth, Occupation, Employer name, Purpose of transaction, Beneficial owner, and Identification number
- Customer due diligence across three levels – Simplified, Basic, and Enhanced
- Continuously monitor your customers’ transactions against the thresholds built into your risk profiles
Also Read: Blockchain technology for KYC: The Solution to Inefficient KYC Process
WCAG
Web Content Accessibility Guidelines is a set of multiple success criteria and guidelines by which web-based apps and websites are considered accessible for people with disabilities and impairments. Keeping the requirements of this industry compliance and regulations in top consideration, we built Avatus – a platform that is today being used by people with special needs with comfort.
- Level A: This is the base level of WCAG, which ensures that all the basic accessibility functionalities are in place.
- Level AA: Level AA addresses a bigger range of accessibility issues. This stage consists of the Level A elements along with other rigorous standards, aimed at improving the accessibility for a wide range of disabilities, comprising error identification and color contrast
- Level AAA: The most exhaustive level, Level AAA consists of all criteria from Levels A and AA, with additional, more rigorous requirements. While aiming for Level AAA adherence, a website should be made highly accessible, something that businesses don’t necessarily need to aim for.
How Regulatory Bodies are Approaching Technology Integrations
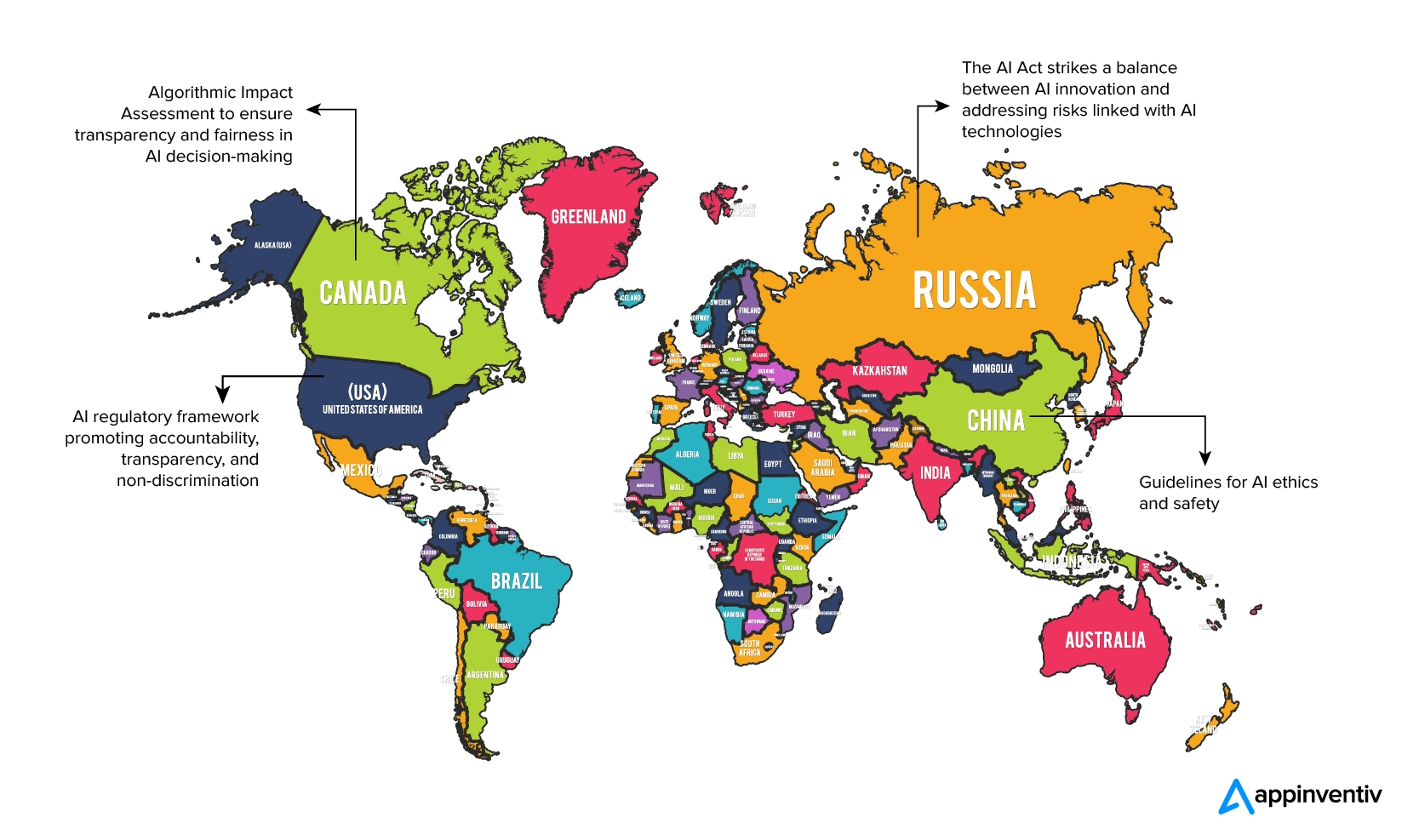
Up until this stage, we have looked at the many industry-level IT compliance and security standards. What is left now, is to look at how the regulatory bodies are approaching technology integrations in digital products. The two technologies we are keeping in focus here are AI and Blockchain.
Globally, a common theme among AI-based regulations is the focus on accountability and transparency. Governments are advocating for building accountability mechanisms addressing biases, safeguarding discrimination, and holding developers accountable for the AI model they are building.
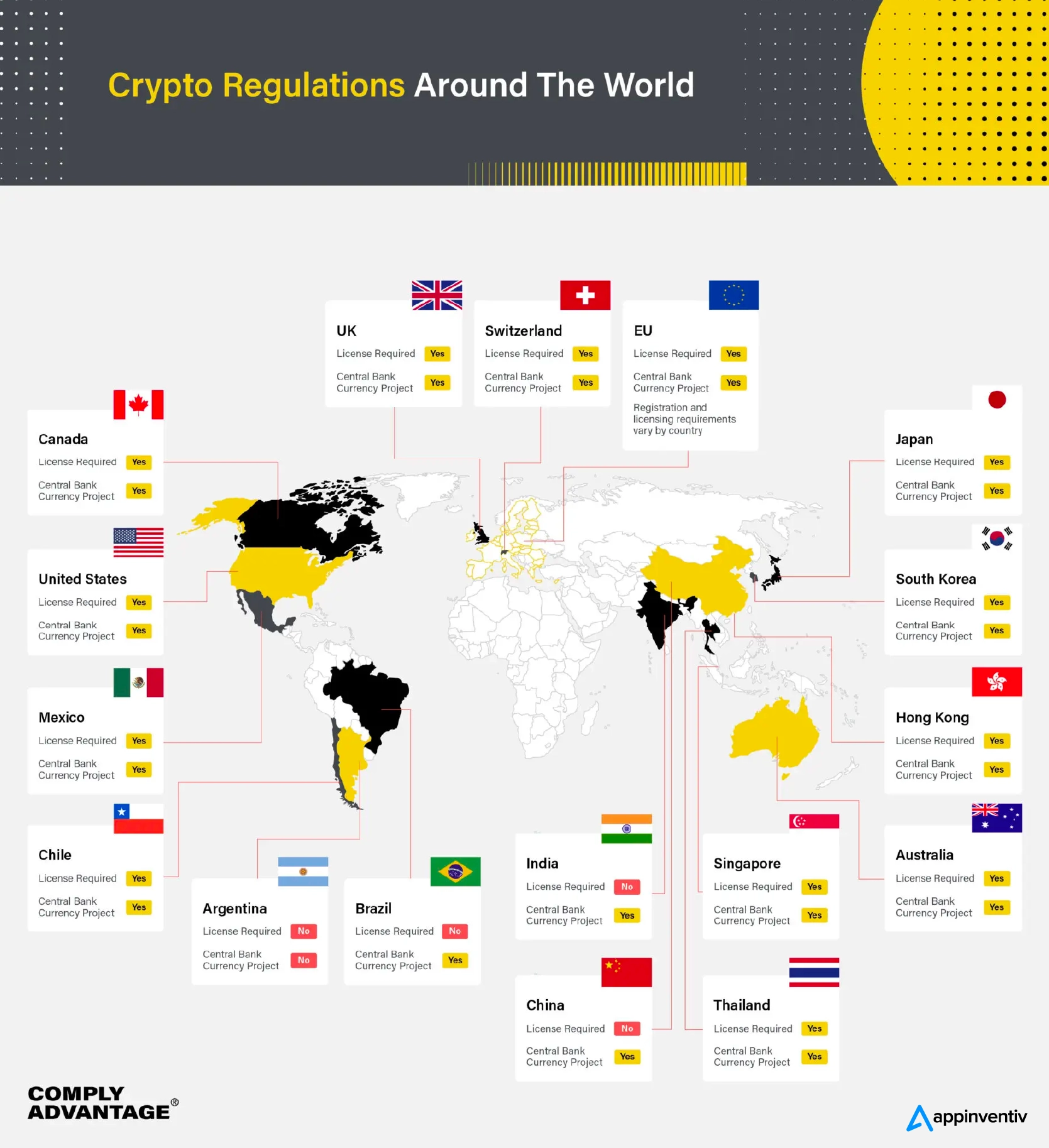
Blockchain has a similar story to share with countries still expanding their regulations to be in line with the innovations happening in the decentralized space. Here’s a look at the country-wise crypto regulations active around the globe
How to Ensure Compliance-Readiness in Product Development?
Having extensively looked into the list of compliances in the IT industry, across different sectors, I am sure you must be wondering how to get started in the compliance-readiness journey. While the short and practical answer would be to find the right partners, depending on which stage you are at in the product life cycle.
Meaning, if you are building a product that will be operational in a compliance-heavy industry, you should partner with an IT consulting services provider like us. We don’t just consult businesses on the ways to be compliant but also have a dedicated subject matter expertise in creating digital products that follow software compliance standards in the US and across the globe.
On the other hand, if you are at a stage where your product is live but is not compliant, you will have two options – either partner with a compliance expert or again a software development agency like us who have worked with multiple compliance-oriented businesses.
Either way, we hope that the article gives you all the information you would need around IT compliance regulations and you will now comfortably come to a stage where you know which regulation is apt for you and what you would need to be adherence ready.
Ready to be compliant with your industry’s top regulatory standards? Get in touch.
FAQs
Q. What is compliance in IT?
A. Compliance in industries including IT is the state of adhering to the policies built by local and global regulatory bodies. For the IT domain, the policies usually revolve around data security when in transit and at rest.
Q. Why does every business need to pay attention to IT compliance?
A. Compliance in the IT industry is crucial for protecting clients, customers, employees, and companies’ privacy and for increasing the trust that the customers have in a business. Moreover, ensuring IT governance in the United States can be seen as having a lasting impact on your business reputation and revenue
Q. How to know which regulation does my business need to adhere to?
A. You will find the answer to adhering to the right IT compliance regulations by looking at your competitors or consulting with a software product development team like ours who have the expertise of working with compliance-heavy industries.


IT Infrastructure Software Development - The Why's and How's
In today's age of digital transformation, where businesses increasingly rely on technology to drive efficiency and innovation, the role of IT infrastructure has become more critical than ever. At the heart of this infrastructure lies software development – a dynamic process that enables organizations to build, deploy, and manage the software systems that power their…
Managed vs. Co-Managed IT Services - Selecting the Right Fit for Your Organization
The fast-paced world of tech continues to propel businesses towards utilizing IT services for improved operations and better output. Consequently, the expenditure on IT services is escalating, with forecasts suggesting a remarkable global figure of $1.585 billion by 2024. This substantial increase highlights the importance of IT services in assisting enterprises to accomplish their goals.…









